In this tutorial we will help you setup Surfshark VPN on your router with the OpenWRT firmware and the new Wireguard protocol.
Surfshark VPN offers a great VPN service, with some great apps to get you up and running on your devices. However we found using and setting up the service on our OpenWRT router quite problematic. The support files at Surfshark are a great help to assist.Please remember this tutorial is for setting up Surfshark VPN to your OpenWRT internet router using the new Wireguard VPN settings.
You must ensure that you have the following for this setup to work
Cable router with OpenWRT firmware already setup with SSH access. Our test router had the OpenWRT firmware V19.07.7
Windows 10 OS computer for setting up our VPN router.
A SurfsharkVPN subscription. Head over here if you don’t have one for some great discounted prices. You will be provided with a great offer using our link here
These are the steps in our blog tutorial below:-
- Step 1 - Goto your SurfsharkVPN account and configure then download your SurfsharkVPN Wireguard profile
And that's it
So lets get started
- Step 1 - Goto your SurfsharkVPN account and configure then download your SurfsharkVPN Wireguard profile
Log-in to your Surfshark account and then on the left go to the VPN tab and choose the Router option and then click on WireGuard.
A new window will open. Now click on I don't have a key pair.
On the next window click on Generate a new key pair.
Note: once the key pairs are generated, copy them and store them on your device, as you will not be able to check them again.
Note: once the key pairs are generated, copy them and store them on your device, as you will not be able to check them again.
Next we need to choose the server location so select Choose a location button, and click on it where you will see a full list of available locations to connect to. Select one and hit the download button.
Then download your profile to your desktop. The file will have the *.conf extension and contain all the relevant information like private and public keys, dns, server location etc information... If this information is missing in your downloaded config file go back and re-create the file or save this information from the surfshark account login manual setup page. This information is required or the wireguard setup will not work. SEE THE YOUTUBE VIDEO at the bottom of our tutorial if you need further assistance.
In our example file below we have taken out our sensitive information like Private and Public keys, Interface, Address, Allowed IP's and Endpoint information.
- Step 2 - At your OpenWRT router install the WireGuard software.
We assume that you have your OpenWrt router already flashed with the up to date firmware and secured with an internet connection available
Open up your internet browser and type in the address bar access for your router setup page. Normally this is 192.168.1.1 unless you have changed this.
Next click on System and select Software.
Now re-boot your router.
- Step 3 - At your OpenWRT router configure / setup Wireguard and the router firewall.
We will now need to configure and setup the WireGuard interface.
Open up your internet browser and type in the address bar access to your router setup page. Normally this is 192.168.1.1 if you haven't changed this.
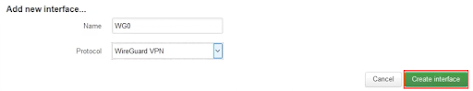
Click on Network, then select Interfaces, and at the bottom of this page select Add new interface.
Type the following in Name and Protocol
Name: wg0
Protocol: WireGuard VPN
And then select Create Interface.
Protocol: WireGuard VPN
And then select Create Interface.
Now in the Newley created wg0 interface we will enter the Private key which we generated at the beginning of this tutorial.
Within the wg0 "General Settings" page Copy and paste the Private Key you saved earlier as shown below. Make sure this is the Private key and not the public one
In the IP Address box, enter the IP address from the Surfshark WireGuard server file you saved earlier. In our example our was 10.14.0.2/16.
Next click on the Advanced Settings tab and uncheck Use DNS servers advertised by peer and enter Surfshark DNS addresses which are: This option may not be available on some versions
162.252.172.57
149.154.159.92
Assigning the firewall Zone
Next we will assign a firewall zone. To do this click on Firewall settings. and then click on unspecified and then in the bottom field enter vpn
Next click on the Peers tab and select Add peer
Now enter all the information as shown below :
Description: you can name it whatever you like. Our example name was SurfsharkWireguardUSA
Public key: paste your public key which is shown on the config file downloaded earlier (NOT private)
Allowed IPs: 0.0.0.0/0
Route allowed IPs: Put a tick in this box ✅
Endpoint host: enter the endpoint IP address of the configuration file (note that it should end with surfshark.com) In our example ours was us-seatle.prod.surfshark.com
Endpoint port: Enter the last 5 digits from the IP address of the configuration file - In our example ours was 51820
Lastly, click Save.
We now need to save and apply the 7 pending changes with in our newly created WG0 interface so that they are saved within our router
Finally we need to Configure the VPN zone
To configure the VPN zone. Go to the Network tab and select Firewall at the bottom.
Finally Click Save & Apply and reboot the router
The WireGuard VPN is should now be active and working. To verify, click on Network, then select Interfaces. The WG0 interface created should be receiving and sending packets.
All now should be working with your internet protected by the Surfshark Wireguard VPN connection.
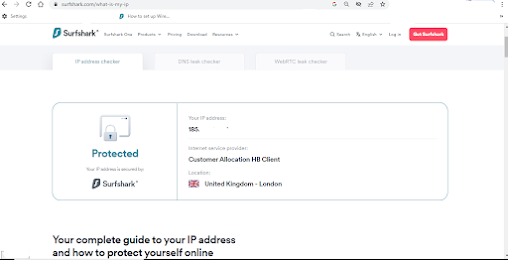
To check that Surfshark is protecting you with a secure connection open up your internet browser and go to https://surfshark.com/what-is-my-ip
This useful webpage will confirm that your connection is secure. You can also carry out the Leak test to check that you using Surfsharks secure DNS servers.
And if you still experience problems head over to Surfsharks Support where they have some great help pages.
An example is this great youtube video below by them which you will find useful
We would like to thank the original author of this review at www.punj.co.uk for granting us permission to publish this particular blog content. The original contents of the review can be found at http://www.punj.co.uk
We are providing the contents here for educational purposes only and offer no guarantee that this process will work for you. On this note you should be aware that by carrying out the processes here you do so at your risk